Brute force attacks
Automated tools attempt to brute force thousands of username and password combinations to gain access

RDP Security Protector protects Windows Server or any Windows computer from brute force attacks over RDP and FTP. RDP Security Protector automatically detects the source of the attack and blocks all subsequent possible hacking attempts. The program works as a service and, in the full version, does not require any administrator intervention. Convenient customization of the RDP protocol protection service allows you to adjust the service to suit the peculiarities and nuances of the local infrastructure and local security policy.
Download
To protect Windows Server from RDP attacks, you must:



Windows Firewall blocks all subsequent bot attacks. If attacks from new IP addresses are detected, they are automatically entered into Firewall rules for blocking.
Note: If you do not have an RDP Security Protector License, a Windows Server or Windows computer administrator needs to manually confirm adding rules to Windows Firewall. You can purchase an annual subscription to the RDP Security Protector License here __

Remote Desktop Protocol (RDP) is an essential tool for every Windows Server administrator, including plain Windows. However, RDP has become a target for cybercriminals who exploit vulnerabilities to conduct password brute force attacks, steal credentials, and compromise Windows systems. RDP Security Protector counters these threats and securely and automatically solves the problem of remote desktop security.
RDP allows users to connect to a remote machine or Windows Server over a local network or the Internet. This is convenient, but it opens up the following potential RDP vulnerabilities:

Brute force attacks
Automated tools attempt to brute force thousands of username and password combinations to gain access

Exploitable ports of default ports
Unprotected or default RDP ports make systems an easy target for attacks

Insufficient security layers
Weak protocols or improperly configured Windows security and protection settings put computers at risk

RDP cybersecurity threats
Unauthorized access can lead to data leakage, ransomware deployment, or a complete takeover of a Windows server
Addressing these and other remote access security factors is necessary to protect secure remote desktop access connections and prevent RDP hacking incidents.
Intelligent detection of attacker IP addresses


The main sign of an RDP attack is repeated failed login attempts from different IP addresses. RDP Security Protector monitors login attempts to detect RDP hacking attempts. When a potential password brute force attack is detected, the program flags the source IP address and subnet of the attack source.
The full version of RDP Security Protector automatically adds detected IP addresses and subnets to Windows Firewall rules to block further login attempts. This remote desktop protection prevents further logon attempts to a Windows system or Windows Server, stopping attackers without manual intervention.
Demo users can see the identified IP addresses of attacking hosts, and then the administrator can manually configure firewall rules. Although this approach is less automated, it provides strong protection against RDP vulnerabilities.
RDP Security Protector like an RDP guard on external circuit of Windows Server or Windows PC. Silent RDPGuard against hacking.
FTP protection against brute force attacks and password brute force attacks
In addition to RDP, RDP Security Protector can protect FTP protocols, providing additional protection for servers managing file transfers. This flexibility makes it a valuable tool for organizations that need comprehensive server protection against FTP attacks.

Automated protection of RDP ports
The full version of RDP Security Protector is an "install and forget" solution that secures remote desktops and Windows and Windows Server computers without constant monitoring

Customizable rules to secure RDP connections
Administrators can flexibly customize rules according to specific security policies, improving their control over secure RDP connections

Integrated reporting
Detailed logs of login attempts and blocked IP addresses provide insight into RDP cybersecurity threats and aid forensic analysis

Ease of use
The intuitive interface simplifies RDP protection even for administrators with limited RDP cyber security knowledge

Scalability
Whether managing a single server or a corporate network, RDP Security Protector adapts to different levels of complexity
Using RDP Security Protector is essential in a broader remote access security strategy. Below are additional ways to secure remote desktop connections and set secure RDP port:
1
Change default RDP ports
Use non-standard ports to reduce the risk of automatic scanning. Change port 3389 to any convenient port in the registry and the firewall settings
2
Enable Network Level Authentication (NLA)
Adding a second level of authentication increases the security of the remote desktop connection
3
Implement Strong Passwords
Require complex, unique passwords to reduce the risk of a successful brute force attack
4
Enable two-factor authentication (2FA)
Add an additional barrier to unauthorized access
5
Regularly update systems
Update Windows Server and RDP clients to fix known RDP security issues
6
Monitor login attempts
Use tools such as RDP Security Protector to monitor and respond to unusual activity
The complexity and frequency of attacks on RDP are increasing all the time, and relying on standard defence and cybersecurity measures may no longer be enough. Other RDP security tools provide some protection, but RDP Security Protector combines process automation, ease of configuration, and ease of use. Here's why it's a better choice:


Advanced remote access security controls: Focused on real-time threat detection and remediation
Easy deployment: Quick installation with minimal customization
Comprehensive protection: Protects against attacks on RDP and FTP protocols and ports
Proven effectiveness: Successfully protects against advanced threats like RDP hacking and brute force attacks
The convenience of RDP should never come at the expense of remote desktop security. Regardless of the number of managed servers, RDP Security Protector is essential for securing remote access, mitigating RDP vulnerabilities, and protecting against cyber threats.

If you're wondering "How secure is RDP?" or "What is RDP in cyber security?" or “How to secure remote access”, remember that its security depends on how well it is protected. By utilizing tools like RDP Security Protector and following remote access security best practices, you can ensure that your servers are resilient to escalating cyber threats.

RDP Security Protector is a reliable solution for securing RDP connections, RDP vulnerability, protecting against RDP attacks, and strengthening remote desktop protection. Don't wait for a secure remote desktop access vulnerability to compromise your systems—take action now!

Q: I cannot connect to a remote Windows Server using Remote Desktop. An error message appears when connecting:
As a security precaution, the user account has been locked because there were too many logon attempts or password change attempts. Wait a while before trying again, or contact your system administrator or technical support.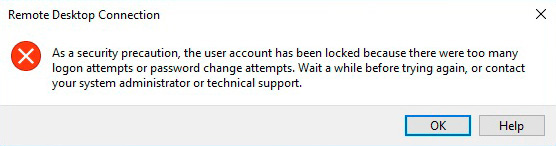
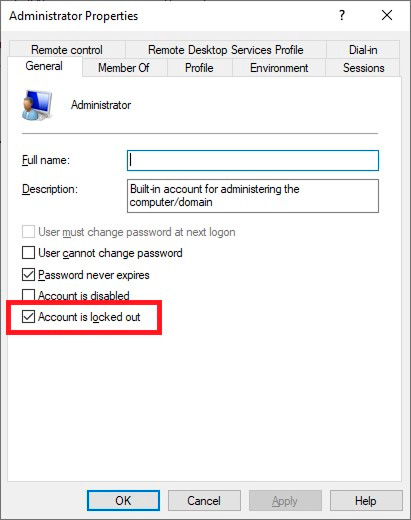
A: This message informs you that Windows Server is currently under a password brute force attack. After a sufficient number of connection attempts with invalid username and password pairs, the user record has been blocked.
Fixing the problem requires: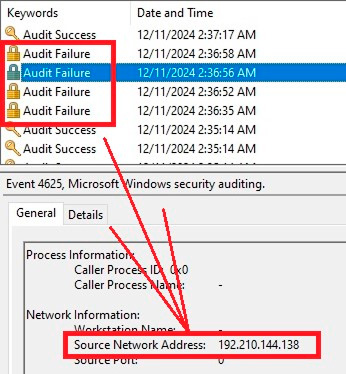
File Master LLC is SaaS of Recovery Toolbox, Inc. Recovery Toolbox, Inc. is an independent software vendor. We develop and distribute the software for restoration of the data from 2003. Member of ISDEF (Independent Software Developers Forum) http://www.isdef.org/en/.
Victor Bobrov CEO of File Master LLCMCSD, MCDBA




Successfully tested on Windows Server 2012 Terminal Edition.
Please add the report generator to PDF file.